 Course Introduction
Course Introduction
Core Standards of the Course
Strand 1
Managing Efficiency and Security
The student resolves common security alerts, diagrams instance states and transitions, and explains how to choose the most cost-efficient instance type
Standard 1
Security Models
This module will give students an introduction to the shared security model as it relates to the three main cloud services. They will understand the responsibilities of the client and cloud service for patching, Operating System updates, and data security using the Shared Responsibility Model.
-
Understand the Shared Responsibility Security Model
- Responsibilities of the customer (for example: customer data, network configuration, applications, IAM, and other responsibilities of security IN the cloud)
- Responsibilities of the cloud service provider (for example: software, regions, hardware, and security OF the cloud)
- Understand the difference between Type I and Type II hypervisors
-
Determine the security responsibility for cloud services
- Prioritize a company's security needs, evaluate the risk, and understand the vulnerabilities
- Understand the Principle of Least Privilege (PoLP) as the concept that the least number of permissions is to be applied to a user
- Where it can be applied, for example:
- a user can search (READ)
- add (WRITE)
- delete (DELETE)
- modify (WRITE and/or DELETE
- To whom does it apply to, for example:
- end users
- systems
- processes
- networks
- databases
- applications
-
Analyze how the shared security model accounts for common threats to the cloud computing model.
Standard 2
Shared Security
Students will be introduced to security assessment services and how to resolve any alerts.
-
Understand the use of a security assessment service
-
Understand the results of a security assessment service, including the five categories: cost, optimization, fault tolerance, performance, service limits, andsecurity
-
List the steps required to resolve an automated security alert
Standard 3
Cloud Services and Instance States
Students will manage instances from launch through termination. Instance lifecycle and transition between states will be introduced.
-
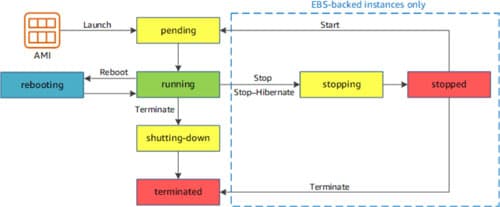
Describe the six instance states and predict the instance state, for example: pending, running, stopping, stopped, shutting down, and terminated
-
Understand which type of virtualization instance can run inside an OS
-
Indicate instance usage billing for each instance state
- On-Demand Instances - billed when used with no long-term commitment
- Reserved Instances - purchased in advanced for a discount, you pay for the entire term regardless of actual use
- Spot Instances - an unused instance that is available at a discount, available for use when available, good for workloads that can be processed at any time
-
Understand the differences between rebooting, stopping, hibernating, and terminating your instance
-
Understand Audit Logs
- List the steps required to resolve an automated security alert
- Determine the most optimal billing option for instances for a company
- Diagram the transitions between instance states from launch to termination
- Determine the most appropriate instance state for a given situation
Strand 2
Creating Cloud Environments to Scale
The student will differentiate between dynamic and static websites.
Standard 1
Dynamic Web Servers I
Students will compare static and dynamic websites
-
Compare static and dynamic website
- Understand the features of each
- Dynamic websites change with user interaction
- Static websites do not change with user interaction
- Understand the features of each
-
Understand the process of setting up a static website
-
Types of dynamic websites
- Built on Content Management Software (CMS)
- Built from scratch
Standard 2
Dynamic Web Servers II
Students will launch and create a dynamic server
-
Understand the purpose of a content delivery network (CDN)
-
Understand how a CDN relates to speed of a website and edge locations (for example: websites using a CDN have faster speeds as data is cached at edge locations, closer to end-users)
Standard 3
Serverless Computing
A cloud service that runs code in response to events and automatically manages the computing resources required by that code.
-
Understand how to create a serverless compute function using a serverless compute console
-
Know the instance lifecycle
-
Understand the chargeback model as it applies to the costs of IT services, hardware, or software
-
Understand purchasing options for instances and usage billing, for example: Pending, Stopped, Shutting-down, Terminated = Not billed, Running = billed
-
Understand the transitions between instance states:
Standard 4
Auto Scaling in Cloud Environments
Student will learn about the functions of auto scaling and create an auto scaling group.
-
Describe the three main functions of auto scaling
- Monitor the health of running instances
- Replace impaired instances automatically
- Balance capacity across availability zones
-
Understand a launch template
-
Understand an auto scaling group
-
Know how to create a plan for monitoring an auto scaling instance or group
-
Understand how to enable syslog forwarding to centrally monitor cloud environments
- Create a content delivery network distribution to increase the speed of a website
- Students will launch a dynamic web server
- Create a launch template and an auto scaling group
- Develop a plan for monitoring an auto scaling instance or group
Strand 3
Managing Cloud Resources: Big Data and Cryptocurrency
Students will learn the benefits and risks of using big data.
Standard 1
Big Data
Introduce the student to the concept of big data and the difference from traditional types of data.
-
Define big data and the "three V's"
- Volume
- Variety
- Velocity
- Veracity and Value (other commonly used "V" descriptors)
-
Evaluate the pros and cons of big data
-
Ethical and legal issues related to big data
Standard 2
Big Data Processing Cycle
Students will learn the big data processing cycle, its activities and challenges of each phase.
-
Understand various types of data
-
Identify the types of cloud migration and conversion methods
-
Understand various types of processing methods
-
Identify the different RAID levels for data storage
-
Understand high availability functionality
-
Understand various types of quality challenges
-
Understand various types of analysis techniques
-
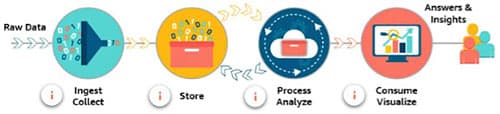
Big Data Processing Cycle phases
- Collect
- Store
- Process & Analyze
- Consume & Visualize
-
Understand the types of data storage
- Big data storage - architecture that collects and manages large data sets and enables real-time data analytics
- Nonrelational databases - a database that does not use rows and columns found in traditional database systems
- Data warehouses - central stores of integrated data from one or more sources
- Data lake - repository of data stored in its raw format
Standard 3
Blockchain and Cryptocurrency
Students will learn how blockchains are created and maintained to support immutability and validity. They will also be introduced to cryptocurrency technologies.
-
Understand blockchain and how they function in the cloud
-
Explain how blockchain ensures the validity an immutability of transactions in the cloud
-
Understand the pros and cons of blockchain busines applications
-
Understand cryptographic hash
-
Understand cryptocurrencies
- Student will be able to access and manage big data from the cloud
- Student will understand the complete big data ecosystem
Standard 1
Artificial Intelligence Capabilities and Impacts
Students will learn about the back end of artificial intelligence (AI).
-
Recognize capabilities of artificial intelligence (ex: image and video analysis, natural language, personalized recommendations, virtual assistants, and forecasting)
-
Understand how AI can enhance the customer experience
-
Analyze the ethical implementation of artificial intelligence
Standard 2
Machine Learning
Students will learn how machine learning can be applied to solving problems.
-
Explain machine learning and how it can help address a need or problem
-
Understand procedures in machine learning and applications used to create ML programming
-
Machine leaning capabilities:
- Recommendations
- Forecasting
- Recognition
Standard 3
Internet of Things
Students will learn how cloud technology facilitates the Internet of Things (IoT)
-
Understand the Internet of Things as the network of common, everyday devices embedded with sensors and communication technologies for sending and receiving data over the internet
-
Types of IoT
- Industrial - building applications for predictive quality and maintenance and to remotely monitor operations
- Home/consumer - building connected home applications for home automation, home security and monitoring, and home networking
- Commercial/municipal - applications for traffic monitoring, public safety, andhealth monitoring
-
Explain the relationship between cloud technology and the Internet of Things
-
Evaluate security and privacy concerns with the increasing IoT usage
- Student will explore AI services and determine which type of AI product would address aparticular issue - some examples could be:
- Amazon Comprehend: discover insights and relationships in text
- Amazon Forecast: increase forecast accuracy using machine learnings
- Amazon Lex: build voice and text chatbots
- Amazon Personalize: build real-time recommendations into your applications
- Amazon Polly: turn text into lifelike speech
- Amazon Rekognition: analyze image and video
- Amazon Textract: extract text and data from documents
- Amazon Translate: translate texts with higher accuracy
- Amazon Transcribe: translate audio files to text
- Students will create a machine learning algorithm
- Student will create a connection to IoT devices
Strand 5
Skills for Career Development
Standard 1
Students will demonstrate positive workplace behaviors that enhance employability and job advancement such as regular attendance, promptness, attention to proper attire, maintenance of a clean and safe work environment, appropriate voice, and pride in work.
Standard 2
Students will demonstrate positive personal qualities such as flexibility, open-mindedness, initiative, listening attentively to speakers, and willingness to learn new knowledge and skills.
Standard 3
Students will employ effective reading and writing skills; solve problems and think critically; and demonstrate leadership skills and function effectively as a team member.
- Communication
- Problem Solving
- Teamwork
- Critical Thinking
- Dependability
- Accountability
- Legal requirements/expectations


 UTAH EDUCATION NETWORK
UTAH EDUCATION NETWORK

 Justin
Justin Braxton
Braxton Dani
Dani Kayla
Kayla Katie
Katie Lora
Lora Rob
Rob Val
Val
